Securing Database and Service Communications
This guide explains how to establish secure TLS connections between Gluesync agents and your databases or services. Proper TLS configuration ensures that all data transmitted between your Gluesync agents and your data sources remains encrypted and secure.
Overview
Secure communication between Gluesync agents and your databases/services is crucial for protecting sensitive data during transmission. Gluesync supports TLS certificate-based authentication and encryption, allowing you to establish secure connections with your data sources.
Setting Up TLS Certificates
Gluesync provides two methods for configuring TLS certificates:
Method 1: Using the Setup Wizard
The easiest way to configure TLS certificates is through the Gluesync Setup Wizard:
-
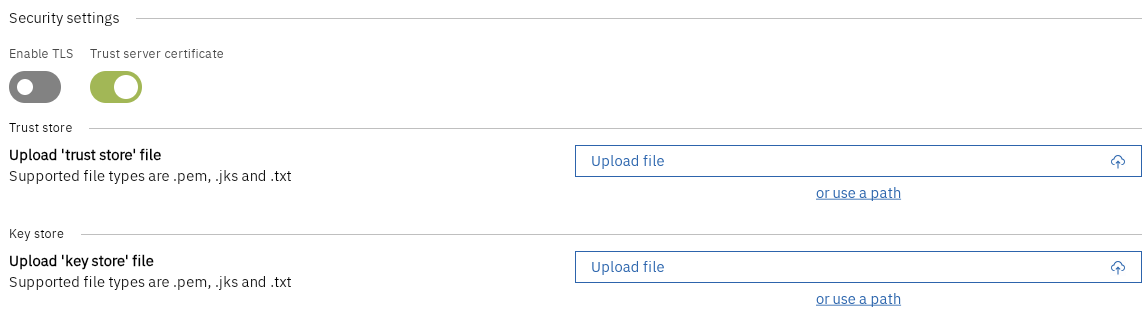
Navigate to the Security settings section in the agent setup wizard
-
Enable TLS by toggling the switch
-
Choose whether to trust the server certificate
-
Upload your certificates:
-
Trust Store file (.pem, .jks, .json, or .txt format)
-
Key Store file (.pem, .jks, .json, or .txt format)
-
Method 2: Docker Volume Mount
For automated deployments or when managing certificates through infrastructure as code, you can mount certificates directly as volumes:
version: '3'
services:
gluesync-agent:
image: gluesync/agent:latest
volumes:
- ./your-certs/truststore.pem:/opt/gluesync/certs/truststore.pem
- ./your-certs/keystore.pem:/opt/gluesync/certs/keystore.pemThe declared certificate path can then be issued to the agent using via the setup wizard or via API (see agent documentation for more information).
Once done, restart the container and paste /opt/gluesync/certs/truststore.pem within the proper property to let the agent read the certificate properly; this is required since hot-mounting doesn’t work in docker.
Certificate Formats
Gluesync supports various certificate formats to accommodate different security requirements:
-
.pem: Privacy Enhanced Mail format (Base64 encoded DER certificate)
-
.jks: Java KeyStore format
-
.txt: Text files containing PEM-formatted certificates
-
.json: JSON files containing security-authentication certificates
Security Best Practices
-
Certificate Management:
-
Regularly rotate certificates before expiration
-
Use strong private keys (minimum 2048 bits for RSA)
-
Keep private keys secure and never share them
-
-
Access Control:
-
Limit certificate access to authorized personnel
-
Use separate certificates for different environments
-
-
Monitoring:
-
Monitor certificate expiration dates
-
Set up alerts for certificate-related issues
-
Troubleshooting
If you encounter TLS connection issues:
-
Verify certificate file permissions
-
Check certificate expiration dates
-
Ensure certificate format matches your configuration
-
Validate trust chain if using custom Certificate Authority
-
Review Gluesync agent logs for TLS-related errors
Swapping built-in CA certificate
If you’re using a custom Certificate Authority (CA) to issue certificates, you may need to swap the built-in CA certificate with the one issued by your CA. To do so, follow these steps:
-
Download the new CA certificate from your CA
-
Upload the new certificate to your agent
-
Restart the agent
To upload the new certificate, you can use the same method as described in the "Method 2: Docker Volume Mount" section, this time targeting the cacerts folder within the agent container:
version: '3'
services:
gluesync-agent:
image: gluesync/agent:latest
volumes:
- ./certs/new-ca.pem:/usr/lib/jvm/zulu21/lib/security/cacerts